This article is more than 1 year old
Mitnick gets hit by Pakistani crackers
Digital graffiti attack targets reformed hacker
Kevin Mitnick, the notorious former hacker turned security consultant and tech celebrity, has been targeted by Pakistani crackers in a series of web face defacements attacks.
Four websites associated with Mitnick's various ventures were sprayed with digital graffiti on Monday in an apparently personal attack. The sites defensivethinking.com, mitsec.com, kevinmitnick.com and mitnicksecurity.com (which all run on Linux, incidentally) were defaced with offensive messages that said "hacking was for homos", among other things. We'll leave it to psychologists to say what that message says about the perps of the attack, but irony obviously isn't their main stock in trade.
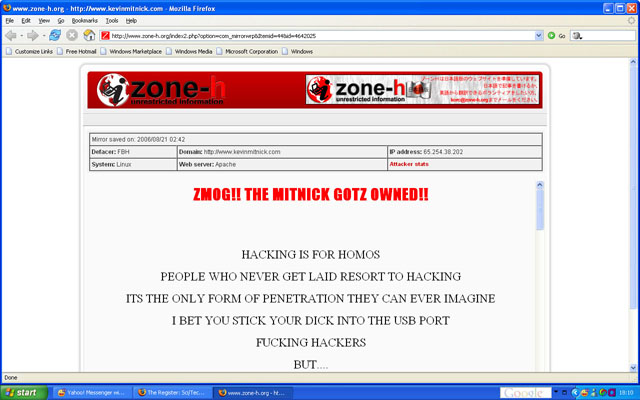
The techniques used in the attacks are unclear but are likely technical in nature, quite unlike Mitnick's stock in trade as a hacker - persuading people to hand over sensitive information through various social engineering techniques, an approach largely pioneered by Mitnick prior to his arrest on hacking offences in 1995.
Mitnick spent five years incarcerated as punishment for attacks against Fujitsu, Motorola, Nokia, and Sun Microsystems, among others, prior to his release in January 2000.
As defacement archive Zone-h notes, Mitnick has been targeted by defacers in the past. Soon after a court-ordered ban on Mitnick that prevented him using computers was lifted in 2003 he set up defensivethinking.com. Its Windows-powered website was defaced repeatedly by different crackers during subsequent months. However, the theme of these attacks (archive of examples here) was more "welcome back Kevin" rather than anything more offensive.
Misconfigured FrontPage extensions were used to carry out these attacks, Zone-h reports. ®
