This article is more than 1 year old
ATI Radeon X1900 XT and XTX
The world's fastest graphics cards?
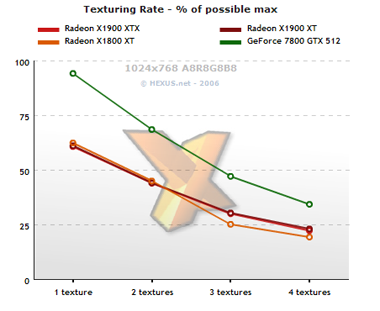
Multi-texture fillrate
Multitexturing is bandwidth-limited as texture layers increase, hence the large lead for the GTX 512. It makes good use of 850MHz memory in this test. Even with the same ROP count, texture units and memory bandwidth as X1800 XT, X1900 XT still exhibits less performance loss, although only to the tune of 3.5 per cent.
Floating-point texture bandwidth
We measure available texture bandwidth by asking the hardware to read from sequential locations in an FP16 texture, the second texel sample relying on the first, creating a dependant texture read.
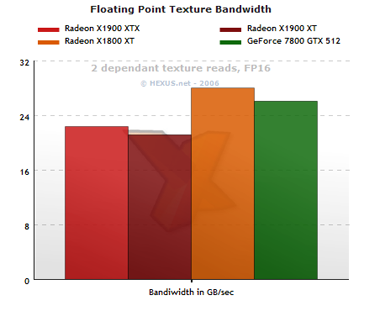
For some reason the hardware can't execute the texture read as fast as the R520 and the X1800 XT can, despite there being no theoretical reason other than a driver problem or issue scheduling the texture fetch. Software defeats the hardware, likely. We'll come back to that theme later.
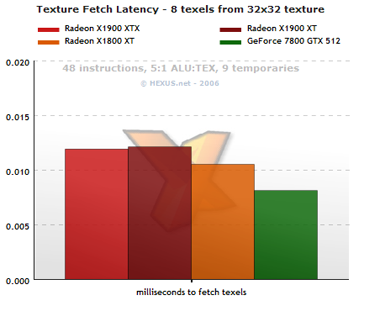
Texture-fetch latency
In our texture-fetch test the R580 is again slightly slower than the R520 when fetching texels from a small texture. The entire texture fits nicely inside the GPU's texture cache on all three tested chips, indicating G70 has a larger texel cache bandwidth than either ATI chip.
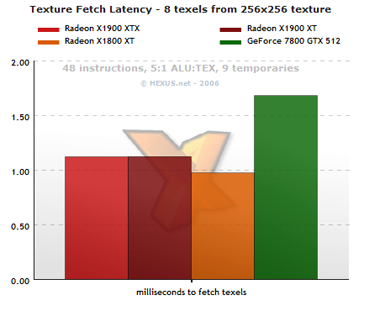
When using a texture that - even with compression - wouldn't fit inside the texture cache, ATI's high-end GPUs do better than the G70, although the R580 is still ever so slightly slower than the R520 at the same clocks.
PCI Express bandwidth
As a nod to the modern GPU's ability to act prefectly well as a generally programmable parallel stream processor, and with R5-series GPUs supporting scatter writes into card memory from shader programs via an OpenGL extension, testing the PCI Express bandwidth of these high-end graphics boards when pushing data back to the GPU is prudent.

The R580 and R520 have over 1000MBps of writeback bandwidth to use, given a suitable host platform. Indeed, the R580 is the first GPU, backed by nearly 50GBps of local memory bandwidth, we've tested that breaks the 1GBps barrier when squirting data back to the host.
