This article is more than 1 year old
Trusted search software labels fraud site as 'safe'
Oops
Digital certificate firm GeoTrust's launch of a search engine with built in trust features this week has been marred by the classification of a phishing site as genuine. Powered by Ask Jeeves, GeoTrust TrustWatch search aims to protect users against fraudulent behaviour and phishing attacks by giving web sites a verification rating. It's a laudable aim, but the classification of a recently created phishing site as "verified as safe" raises serious doubts about the effectiveness of the technology. Such incorrect classifications create a false sense of security that can only play into the hands of would-be fraudsters.
The bogus site purports to represent the Metropolitan Credit Union. It's a crude facsimile of the real site, but TrustWatch assigns the dodgy site a trusted status. Netcraft doesn't score much better in assigning the same ropy site with a risk rating of only "one", a single notch above trusted.
After learning the site was bogus, GeoTrust quickly blacklisted the suspicious destination. To its credit, it also worked with the US hosting firm that unwittingly hosted the site to remove it from the net, but that still leaves the question of how a fraudulent site (screen capture below) came to be awarded a trusted rating in the first place.
Chris Bailey, CTO of GeoTrust, explained that the domain used by the site had previously been verified as trusted. "It's unclear if this phishing site was economically active. In any case, it's now been taken down by the hosting company. It seems there was an insufficient amount of vetting," he said. The url associated with the phishing site has been blacklisted while other sites on the domain have been stripped of their trusted status.
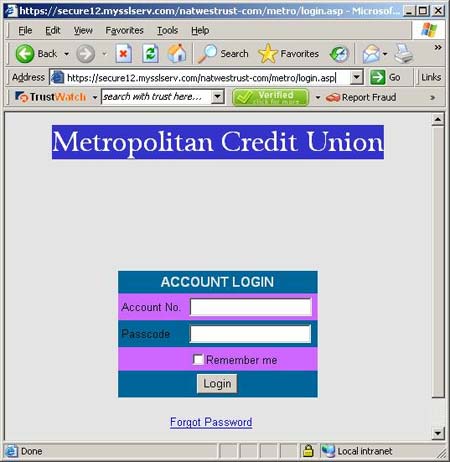
Bailey said that the false classification of a fraudulent site as trusted by TrustWatch was "rare" and said ours was the sole such report. He added that the firm had set up a mechanism for users to report problems and claimed that TrustWatch will become more reliable as more users come on board. Feedback is reviewed, forwarded to anti-fraud organisations, aggregated and may be used in future TrustWatch ratings. An estimated 100,000 users have downloaded beta versions of the software prior to the launch of TrustWatch, the third generation of GeoTrust's anti-phishing toolbar, on Monday (26 September).
The inappropriate classification of a bogus site illustrates the early teething troubles of anti-phishing technology that may take some time to resolve. This is a shame because we found GeoTrust's technology otherwise well designed and easy to use.
The software is free and comes either as a component to GeoTrust's anti-phishing tool bar for Internet Explorer (no Firefox version yet) or by visiting TrustWatch.com. User search results generate green, yellow and red verification symbols beside each search result. Sites that can be verified by trusted third parties receive a green 'verified' rating; sites that have not been verified, but are not known to be fraudulent, receive a yellow 'not verified' rating; and known fraudulent sites display a red 'warning' rating. For the record El Reg gets a far from reassuring "not verified" rating from GeoTrust. Netcraft, by contrast, gives El Reg the green light.
TrustWatch Search is based on GeoTrust's identity verification technology. In addition, TrustWatch Search also works with leading providers of blacklist data, such as Cyota and the Anti-Phishing Working Group, to alert warns consumers about potentially fraudulent sites.
As we've discovered, it's not quite as simple as that so it's just as well there are mechanisms in place to quickly deal with anomalies both for consumers to report suspicious sites and for the manual review of wrongly-classified sites.
GeoTrust's technology is touted as a way for consumers to both find and evaluate the reliability of ecommerce outlets. For example, users can type queries directly into the search box on the TrustWatch toolbar. The Ask Jeeves search engine will return relevant search results alongside TrustWatch ratings. TrustWatch Search also provides a 'Site Report' link via which users can click to get more information about web merchants based on information from BizRate (for Website reviews and store ratings), TRUSTe (privacy policy data), ScanAlert (security audits database) and Alexa (traffic rank information). ®
