This article is more than 1 year old
Dell in front line of War on Terror™
No PDAs for al-Qaeda, that's for sure
We're relieved to report today that al-Qaeda will not be sourcing PDAs online from US websites, well not from Dell at least.
Reader Stephen Mills alerted us to the company's stringent security checks which vet potential purchasers. As a result, we can sleep sounder in our beds safe in the knowledge that Osama bin Laden will not have the comfort of reading the new Register Mobile in whichever stinking hole in the ground he is currently occupying.
To demonstrate how the thing works, we signed into Dell's e-shop this morning using a fictitious US address and chucked the first PDA we saw in the shopping basket. On proceeding to the checkout, we were asked some probing questions, these included:
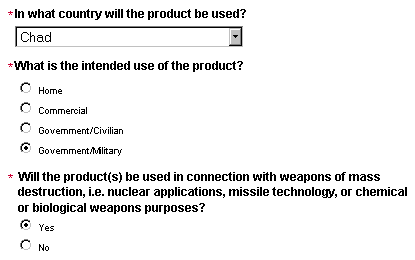 |
Being an honest terrorist organisation, we frankly stated that the PDA was for export to Chad (Afghanistan, Iraq, Libya, North Korea and Syria being unavailable as options), that the intended use was government/military and that the product would indeed be used in connection with weapons of mass destruction.
Having pressed "continue" with some trepidation, we fully expected that, after a suitably dramatic pause, heavily-armed SWAT teams supported by spooks bearing a one-way ticket to Guantanamo Bay and nuke-laden stealth aircraft would surround the building demanding immediate surrender.
But no. Instead we were invited to proceed to the payments page and enter credit card details for immediate shipment. It was at this point that we made our excuses and left the Dell website.
Of course, it's likely that Dell's cunning plan involves taking the credit card payment for intelligence-gathering purposes and then sending in the helicopter gunships.
Either way, it would clearly take all of the cunning and guile of an evil criminal mastermind to penetrate such online defences. We salute Dell and its constant vigilance. ®
