This article is more than 1 year old
Codebreaker II The torture ends
The winners, the solution, the whole shooting match
Well, it's been a long, hard slog for our Reg codebreakers. After weeks of sleepless nights and hair-tearing angst, 32 bright sparks eventually cracked our code.
Readers will recall that the prizes consisted of 10 copies of In Code, by Sarah Flannery. However, so impressed were we by your efforts that we have decided to award prizes to all correct entries. The winner will receive the book, an exclusive 'Show us the money' t-shirt, a much-coveted Register lapel pin and two tickets to Bletchley Park. Books go to the next nine correct entries received. We then have ten pin winners. The last 12 correct submissions are rewarded with a Reg baseball cap.
Congratulations to all of the following:
Winner: Mark Wutka
Books:
Jim Gillogly
Carsten Saager
David Crocker
Niclas Carlsson
Brian Brown
Ivan Kelleher, Cal Corkery and Colin Healy
Paul Grayson
Conan Farrell
Rob Edwards
Pins:
David Hunter
Helge Horch
Scott Lowe
Dan Girard
Olivier Dorey
Chris Dickins
John Elder
Chris Card
Graeme Falkner
Per Liboriussen
Reg baseball caps:
Ian Welch
Ladislav Sladecek
Frank Klevenhaus
Stewart Ramsay
Glenn DeCesare
Brian W. Brown
Robert Mullen
Victor Leverenz
Andre Bossel
Craig Longhurst
Jens
Graeme Ellis
Now, how about that encryption? As all of the above know, the solution to the competition is:
After accidie wol I speke of avarice and of coveitise, of which synne seith Seint Paul that "the roote of alle harmes is coveitise." Ad thimotheum sexto. For soothly, whan the herte of a man is confounded in itself and troubled, and that the soule hath lost the confort of God, thanne seketh he an ydel solas of worldly thynges. Avarice, after the descripcioun of Seint Augustyn, is a likerousnesse in herte to have erthely thynges. Som oother folk seyn that avarice is for to purchacen manye erthely thynges, and no thyng yeve to hem that han nede. And understoond that avarice ne stant nat oonly in lond ne catel, but somtyme in science and in glorie, and in every manere of outrageous thyng is avarice and coveitise
A lovely bit of Chaucer (from The Parson's Tale), and a cautionary tale to boot.
First of all, we encrypted this ditty using the substitution code from our original Codebreaker competition. The key is, naturally, 'show us the money':
a = s
b = h
c = o
d = w
e = u
f = t
g = e
h = m
i = n
j = y
k = a
l = b
m = c
n = d
o = f
p = g
q = i
r = j
s = k
t = l
u = p
v = q
w = r
x = v
y = x
z = z
The result is as follows:
stluj soonw nurfb nkgua uftsq sjnou sdwft ofqun lnkuf trmno mkxdd ukunl mkund lgspb lmsll mujff lufts bbums jcukn kofqu nlnku swlmn cflmu pckuv lftfj kfflm bxrms dlmum ujluf tscsd nkofd tfpdw uwndn lkubt sdwlj fphbu wsdwl msllm ukfpb umslm bfkll muofd tfjlf tefwl msddu kuaul mmusd xwubk fbskf trfjb wbxlm xdeuk sqsjn oustl ujlmu wukoj ngonf pdftk undls pepkl xdnks bnauj fpkdu kkund mujlu lfmsq uujlm ubxlm xdeuk kfcff lmujt fbaku xdlms lsqsj nounk tfjlf gpjom soudc sdxuu jlmub xlmxd euksd wdflm xdexu qulfm uclms lmsdd uwusd wpdwu jklff dwlms lsqsj noudu klsdl dslff dbxnd bfdwd uoslu bhplk fclxc undko nudou sdwnd ebfjn usdwn duquj xcsdu juftf pljse ufpkl mxden ksqsj nousd wofqu nlnku
Obviously, the punctuation has been discarded. We have arranged the resulting output above into five-letter groups. There's no necessity for this, but it makes it relate better to the next stage of the encryption.
We then added the phrase 'so far so good' to the end of this encrypted text. Without this, anyone who had successfully cracked the second level of the encryption would have no indication of success - rather just an incomprehensible jumble of letters.
We next ran the text through Andy Lauwers' excellent Windows-based emulator of the 3 rotor service Enigma machine, which you can download here.
We set the machine up thus:
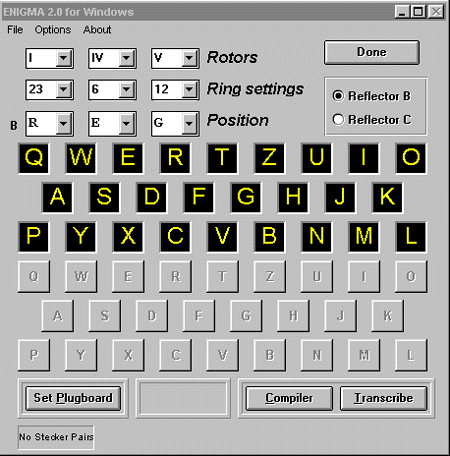 |
Naturally, we decided to fiddle around with the plugboard a bit:
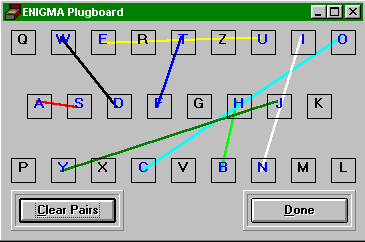 |
Note that the pairings...
S = A
H = B
O = C
W = D
U = E
T = F
N = I
Y = J
...are taken from our substitution code (we've not listed all the letters).
Finally, this is the output as it appeared in the competition. The five-letter groups are created automatically by the Enigma emulator:
TQHYP WQZYP RYCCA YFRAB SGOTK UUSKY KAVQK WNUKQ ZUQJB HHGDE RTVYJ TITVQ QIAMU FNZGR OWDUQ PIOAN KBVZV ESFLU GPRGD GAZFG LHXPT UEQPX JDERH YABXJ VLYNG RCEHQ AUKGY AGSRI RWJRA FWHEZ QNAGX LESQX JPRWT WYFWS HSCAA VOCWZ RYYGN IWOEZ QXOVL OAOFI JSRWG PBEAJ NAFYU GITZO UINEM CQNFX BTOEF UXIWB LPLHD HEGIR DVHSV VTJDY GLYGR SGHZN VXTHY JXYZW ELKFW RCAJH NVEAQ BNIYP LPUTQ FWUPI DLMXY JWQLU WPINZ CMUCT STATG QXBGS RLHTT UQLDD QTIFU KOZXK HBKRC ZAOHC WTVCX NULNC ICTBL YBTET RXJQW RONKU WBOEQ OSFLY QBIEY VRLVB UCUBK CFSSK JKILF LCGPU MKIAW DINAT SEVSY FDUXR GHSCE EQOQM OTJMX AHDBG IVHPV RWNIX MFDFJ HGPZU KFTHH PGNZM CZXAQ SLPMG ZORIO GXCFE RHUFI OYRFY HMSQV AUYXT DPQVT YNBBR XRYIS MGPCD VKKUJ MJCDZ AAIZC P
Well, this competition provided hours of fun for all the family. It also kept paid employees from their work, students from their studies as well as reducing grown men to tears. We hope you enjoyed it and ask you to watch out for Codebreaker III later in the year.
Codebreaker II in full
The original competition
A helping hand...
Cracked it!
